Strategies Doxim employs to provide enterprise-grade security around customers’ Personal Identifiable Information (PII)

Customer communications are an integral part of any organization’s broader customer experience (CX) strategy, and often a regulatory requirement as well. Generating and delivering these essential documents often requires that you share customer data with a vendor, making you reliant on that vendor to protect your customers’ sensitive information just as carefully as you do.
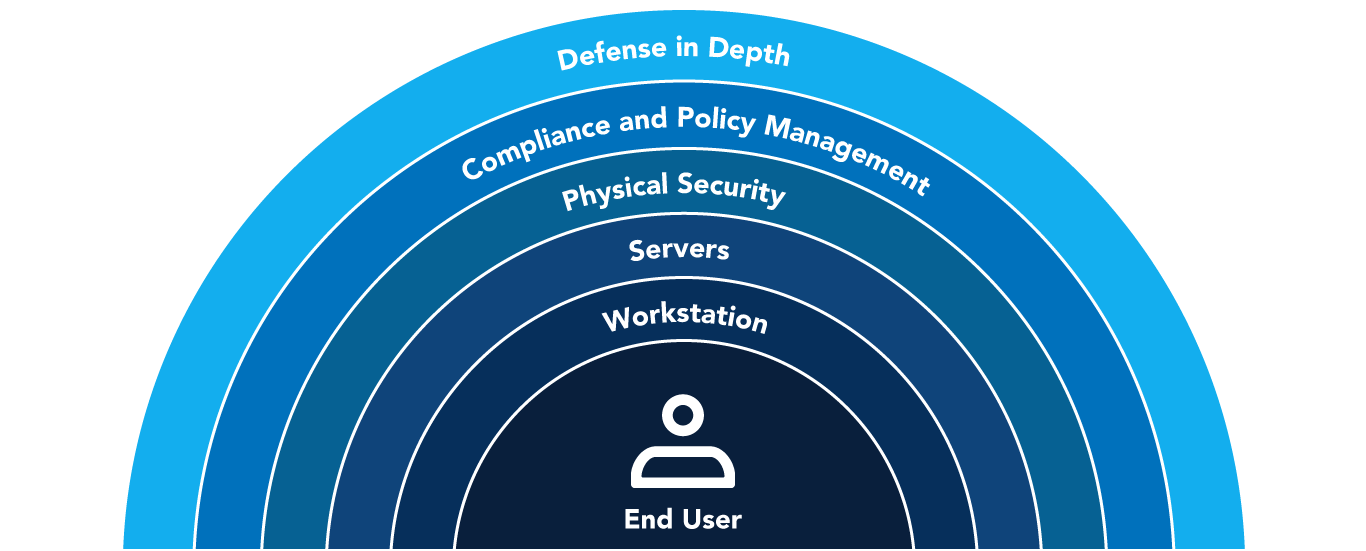
That’s why understanding the steps your customer communications management (CCM) and customer engagement vendor takes to preserve data privacy and security is so important. At Doxim, we take a layered approach to customer data security.
Below, you will learn about some of the strategies we employ to provide enterprise-grade security around customers’ Personal Identifiable Information (PII).
A Layered Approach to Security and Compliance
Doxim’s comprehensive information security program takes a layered approach to security and compliance, including the following high-level approaches, which are discussed in more detail below:
- Instituting security and compliance technologies and processes
- Monitoring 24/7 and addressing threats and vulnerabilities
- Adherence to OWASP development security practices to reduce the risk of vulnerabilities within our technology
- Preparing and regular testing of response measures
- Ongoing training of our associates in physical and digital security measures
Data Availability & Physical Security
Doxim maintains an extensive network of data centers across the nation and around the globe, all fully equipped to meet critical security requirements. Our data centers are strategically located to support an efficient and effective business continuity plan, along with a variety of deployments,
including on-prem, co-location, as well as private and public cloud. Doxim software and client data, as well as systems and protocols in our data centers, are regularly audited to ensure security, processing integrity, confidentiality, and privacy. Our security posture exceeds industry standards and is verified by third parties as top-ranked across all criteria.
Doxim’s state of the art print facilities are highly secure physical environments. We continue to invest in our governance, risk, and compliance (GRC) platforms, enabling us to track compliance, provide security awareness training and conduct awareness exercises with our employees.
Data & Print Redundancy
Doxim’s data centers maintain replication capabilities in accordance with client SLAs and requirements. Doxim print facilities, located from coast to coast in North America, offer customers the security of knowing that their critical print services will be available even during business disruptions.
Customers can also ensure communications continuity with the Doxim Business Continuity (BCS), which allows them to leverage a backup composition, as well as a print and digital communications plan to get back up and running fast.
Connect with our experts today to learn more about Doxim’s Business Continuity Solution. Book a personalized consultation
Application-Level Security
Doxim adheres to OWASP development security practices to reduce the risk of vulnerabilities within our technology.
- User access control – A role-based user permission system controls access to the application and the hierarchical tree structure allows for tiered access levels.
- Separation of roles – The application splits privileges into several roles. Each element of the application’s features has its own roles, such as ‘view’ or ‘edit’, which can be
assigned to different levels of users that administer the
system.
- Access logging and reporting – User actions are logged by the platform for audit purposes. While all services generate log files, the quantity and type of information
that is recorded is configurable
Prior to every software release, each SaaS application is subjected to vulnerability and penetration testing using a variety of attack scenarios.
Vulnerability Assessment and Automated Monitoring
Doxim deploys multiple enhanced external vulnerability scanning tools that alert for new security or application vulnerabilities within our operations. These regular vulnerability and penetration assessments are conducted against applications and environments to ensure
configurations are up to date and new vulnerabilities are patched.
Our security team also manages a program of automated security scanning tools that monitor the production network for suspicious activity. These scans ensure network and infrastructure assets remain free of vulnerabilities and malicious activity.
Technical Controls to Protect Infrastructure and Data Privacy
Doxim incorporates a variety of technical controls to protect the underlying server and its data. These include, amongst others, an EDR solution that is monitored 24×7 by a managed SOC team that are constantly on the lookout for any malicious acts performed via phishing or with intent from threat actors. In addition, Doxim uses a SIEM solution that includes intrusion detection, log event grading based off NIST framework, file integrity monitoring and compliance monitoring. This works hand in hand with the company’s threat monitoring program and continuous vulnerability assessment.
Security & Service Audits and Certifications
Doxim’s documented security policies provide a comprehensive policy framework that address the full
range of required compliance and regulatory controls with regards to data privacy, security, retention, protection and accountability. Many of our policies and procedures also map to NIST controls.
Doxim maintains an annual external audit schedule for environments and SaaS products to comply with standards such as SOC 2, ISO 9001, ISO 27001, PCI DSS and HIPAA, depending on location.
For audit compliance, we perform security awareness and privacy training upon hire and annually for all employees, and phishing tests are performed throughout the year.
Data Privacy Regulations
As a digital communication specialist, we are entrusted with the personal information of your customers in order to provide our services. This requires that we comply with the data privacy and electronic communication laws in the jurisdictions in which we process that data, as well as any regulations agreed by the authorities in those territories.
Doxim security policies provide a comprehensive policy framework that addresses the full range of the required compliance and regulatory controls with regards to data privacy, security, retention, protection and accountability.
State of the art communications from a data privacy and security security champion

The promise of security you provide to your customers is our promise too. At Doxim, we take our responsibility to protect our clients’ sensitive information very seriously. That’s why 2,800 clients across North America, Europe, Africa and Asia trust Doxim’s customer communications management and customer engagement solutions.
Clients in banking, wealth, healthcare, insurance, utilities and government are partnering with Doxim to optimize their customer communications to serve their customers better. Why not join them to experience the value of state-of-the-art communications with the assurance of enterprise-grade security and compliance?
Review Doxim’s data security measures here. Schedule your personalized consultation and demo today







